On December 17th, 2015, Juniper Networks published an Important Announceme
The backdoor can be exploited by using random username and backdoor password through SSH and Telnet.
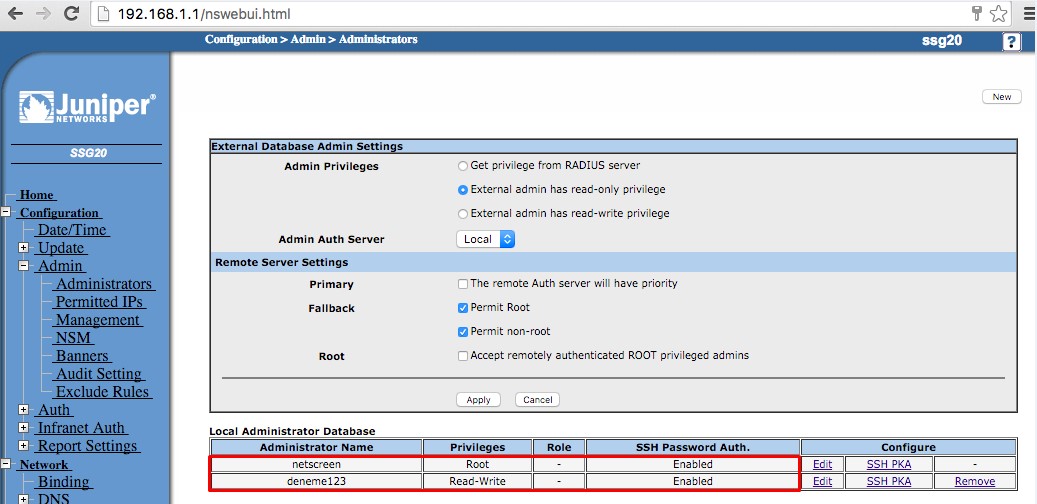
- On lab environment, I tested ScrenOS 6.3.0r17 version on SSG20 brand and the result was stunning. As seen below, only two user was created on the device.
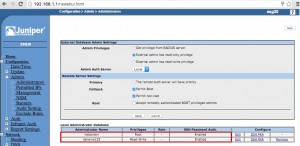
- If the device is vulnerable, you should reach highest privileges on the device.
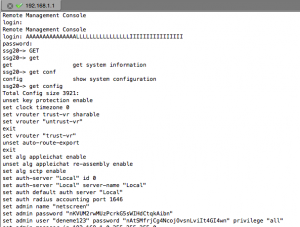
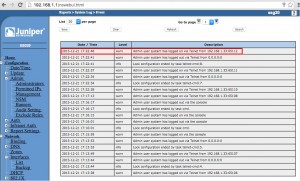
- Upon exploitation of this vulnerability, the log file would contain an entry that ‘system’ had logged on followed by password authentication for a username. Out of Cycle Security Bulletin
Finally, I also tested the some other versions such as 6.2.0r9.0 and 6.2.0r5.0, it is observed that they don’t have backdoor vulnerability.
Bileginize kuvvet , yeni yazı dizilerinizi merakla bekliyoruz.
Teşekkürler.