Detecting and Blocking DNS Tunneling
DNS (Domain Name System) is the protocol which is composed of hierarchical and dynamic database and it provides us IP addresses, text records, mail exchange information (MX records), name server information (NS records).The Domain name system’s protocol concepts, facilities, specification and implementation were defined in RFC 882 and RFC 883. These RFCs were made obsolete by RFC 1034 and RFC 1035 and have been updated by multiple RFCs over the time. (i.e. RFCs 1101, 1183, 1348, 1876, 1982, 2065, 2181, 2308, 2535, 4033, 4034, 4035,4343, 4035, 4592, 5936)
Today, I am going to talk about detecting misuse of DNS protocol, is called as DNS tunneling. In most of the companies and topologies users can access local DNS servers which is capable of performing recursive queries to Root Name Servers. With aid of this tunneling method, another protocol can be tunneled through DNS. A DNS tunnel can be used for ‘command and control‘, data exfiltration or tunneling of any IP protocol traffic. Further more, it is easy to bypass payment canceled Internet services that allow DNS requests but not other traffic until payment is made.
There are several DNS tunneling tools using different record types and encoding methods. Some of them are Iodine, OzymanDNS, dns2tcp and so on.
On lab enviroment, I try to analyze the tool IODINE (Ip Over DNS Is Now Easy ), that has ability to detect the best possible query type and encoding methods. And, I realize that Intel Security product McAfee NSM with default signature set can not even detect the misuse. To prevent this violation, I wrote some custom signatures based on my observations.
- Firstly, It can be verified from the help that Iodine can use seven different queries and four different encoding types.

To analyze the behaviour of Iodine, I investigated every query type one by one.
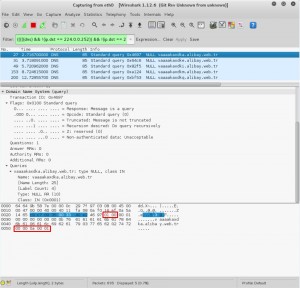
- In this document, I am going to analyze only Null type queries. Null type is not common DNS traffic and is indicative of DNS tunneling. Specifying a treshold could help us to block it.
- The custom signatures I wrote means that;
- Start looking for the pattern “01 00” after 2 bytes and within 4 bytes depth of the payload . This pattern points the packet that contains recursive query.
- And, start looking for the pattern “00 00 0a 00 01” after 12 bytes and within 255 bytes depth of the payload . This pattern points the packet that contains NULL type query.
- If two conditions occur 10 times in 5 seconds from the same source IP, generate an alert.
alert udp any any -> any 53 (msg:"High NULL requests - Potential DNS Tunneling"; content:"|01 00|"; offset:2; within :4; content:"|00 00 0a 00 01|"; offset:12; within:255; threshold: type threshold, track by_src, count 10, seconds 5; sid: 5700001; rev: 1)
You can find the signatures below for other types of DNS queries. But, it is very important to specify count and time variables with respect to your DNS traffic volume.
alert udp any any -> any 53 (msg:"High TXT requests - Potential DNS Tunneling"; content:"|01 00|"; offset:2; within :4; content:"|00 00 10 00 01|"; offset:12; within:255; threshold: type threshold, track by_src, count 10, seconds 5; sid: 5700002; rev: 1;)
alert udp any any -> any 53 (msg:"High CNAME requests - Potential DNS Tunneling"; content:"|01 00|"; offset:2; within :4; content:"|00 00 05 00 01|"; offset:12; within:255; threshold: type threshold, track by_src, count 10, seconds 5; sid: 5700003; rev: 1)
alert udp any any -> any 53 (msg:"High SRV requests - Potential DNS Tunneling"; content:"|01 00|"; offset:2; within :4; content:"|00 00 21 00 01|"; offset:12; within:255; threshold: type threshold, track by_src, count 50, seconds 5; sid: 5700004; rev: 1)
alert udp any any -> any 53 (msg:"High MX requests - Potential DNS Tunneling"; content:"|01 00|"; offset:2; within :4; content:"|00 00 0f 00 01|"; offset:12; within:255; threshold: type threshold, track by_src, count 40, seconds 5; sid: 5700005; rev: 1)
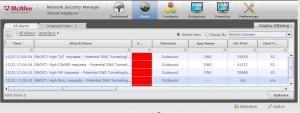
Finally, On McAfee NSM you are going to see the following alerts.
In default, Snort signatures are going to be disabled. You should enable blocking on the signatures after specifiying tresholds.

Uzun zamandır aradığım döküman ! Eline sağlık!