Unknown Unicast Floods As a Local DOS
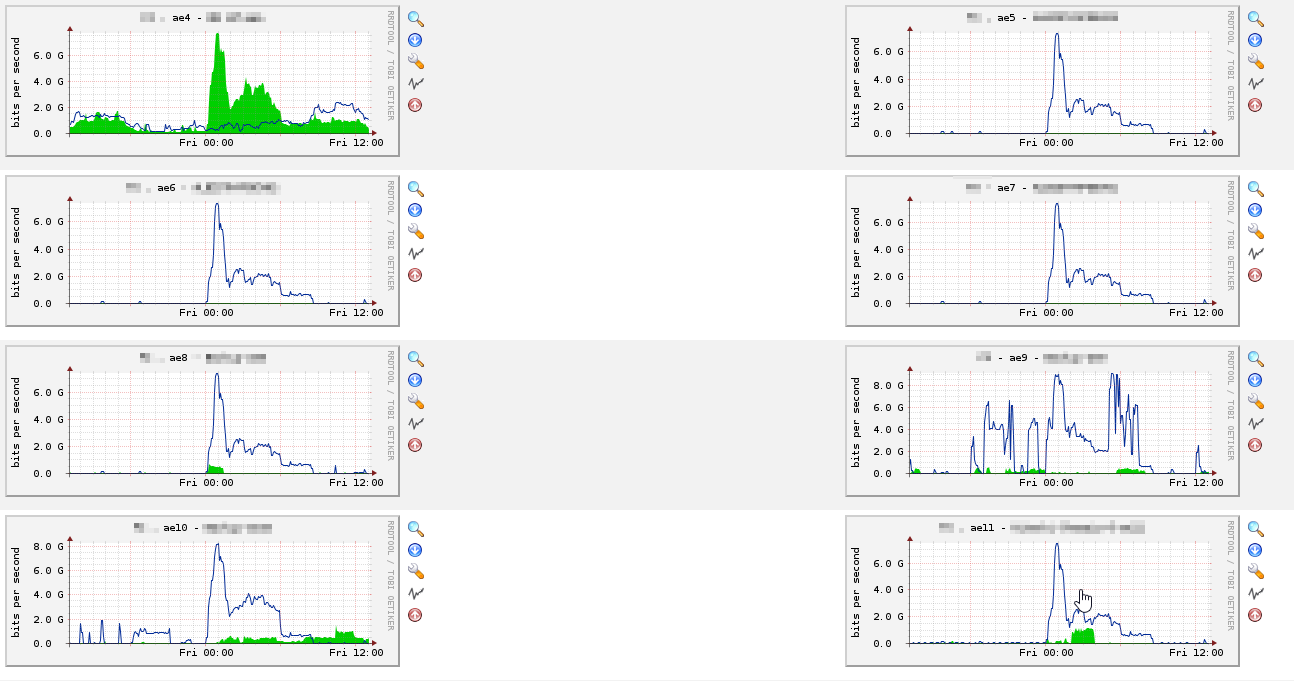
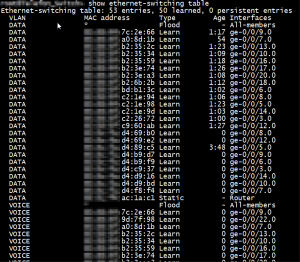
In the last three months, I faced with a problem on my Layer 2 topology. The problem behaved like a broadcast attack and about 10Gbps backup traffic was seen in all related ports of a vlan as seen below.
And, finally we found the root cause of the problem which depends on unknown unicast flooding. Somehow MAC addresses are flapping in approximately every 10 ms. In that duration whole traffic which has the flapped destination MAC address is going to be flooded to whole related ports. Juniper hasn’t pointed it out yet. For a temporary solution, I relocated whole ports to a different switch family.
After finding temporary solution, I wondered that what If I flood the switch with random unknown destination mac addresses? The switch is going to flood all packet with unknown destination mac addresses to whole broadcast domain. Because of this reason, every single switch port is going to be saturated and throughput of the switch will be nearly overloaded.
Today, I am going to talk about unknown unicast packets and its effects.
Basically, there are four different types of communication of packets over networks. Those types are unicast, broadcast, multicast and anycast. Today, we are going to deal with unicast one.
Unicast is the type which describes the communication towards to a single receiver which is identified by a unique (IP or MAC) address.
Broadcast is the type which describes the communication towards to whole endpoints those are assigned to same vlan or same broadcast domain. In order to broadcast a message, destination MAC address must be “ff:ff:ff:ff:ff:ff”.
Being Familiar About the Behaviour of Switches
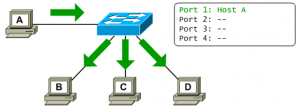
Network switches records the MAC address, its corresponding switch port location and associated Vlan of every single incoming frame. And store these informations into a table called as CAM (Content Addressable Memory). The CAM table keeps these informations about 300 seconds and is used in Layer 2 switching for the aim of quickly switching frames to their destination.
Finally check destination MAC of the the frame from CAM table and specify the outbound ports. Then send the packet to related port.
What Does Switch Do When It Receives a Unicast Frame?
When a switch receives a unicast frame;
- First, it records the source MAC address to MAC table,
- Then, check the destination MAC address whether it has been already learned from any switch port location or not;
- If it was learned before, send the frame out to the related switch port,
- If not, the default behavior is to flood the frame out all other ports associated with same vlan. It is called as unknown unicast flooding or forwarding. “Only after learning of the address as the source of an incoming frame will be entered into the address table with its corresponding port, allowing future frames destined for this address to be forwarded normally as unicasts”.
Flooding the Switch with Unknown Unicast Frames
To realize what I am thinking about flooding, I use MZ (Mausezahn) with following line.
mz -b rand -B 8.8.8.8 -t tcp "flags=syn,dp=80,sp=23467" -p 1400 -c 0
-b : <Dst_MAC|keyword> Same with destination mac address.
rand : Use a random MAC address.
-B : <Dst_IP> Send packet to specified destination IP or domain name.
-p <length> Pad the raw frame to specified length (using random bytes).
-c <count> Send the packet count times (default: 1, infinite: 0).
It will generate about 1 Gbps (depens on your port speed and server’s hardware) traffic to trigger unknown unicast flood. If you have a 48 port switch assigned in a same vlan with you, there is going to be approximately 48 Gbps of traffic to flood.
It will really affect the performance of the core switch and it will saturate the whole related ports. It means outages and performance bottlenecks will occur on your network.
How Do We Defend ?
For Cisco devices;
- Unknown Unicast Flooding Blocking(UUFB)
By default, unknown unicast and multicast traffic is flooded to all Layer 2 ports in a VLAN. You can prevent this behavior by using the UUFB feature to prevent this traffic. The UUFB and UMFB features block unknown unicast traffic flooding at a specific port, only permitting egress traffic with MAC addresses that are known to exist on the port.
- Unknown Unicast Flood Rate-limiting (UUFRL)
Traffic storm control (also called traffic suppression) monitors incoming traffic levels over a 1-second traffic storm control interval and, during the interval, compares the traffic level with the traffic storm control level that you configure. The traffic storm control level is a percentage of the total available bandwidth of the port. Each port has a single traffic storm control level that is used for all types of traffic (broadcast, multicast, and unicast).
For Juniper devices;
- Juniper has similar UUFB and UUFRL, but it also has a feature which allows a VLAN to forward all unknown unicast frames to a specific port (trunk), and each VLAN can use a different port in order avoid overloading a particular trunk.
To do this, you can disable the flooding of unknown unicast packets to all VLAN interfaces by configuring one VLAN or all VLANs to forward all unknown unicast traffic to a specific interface. This channels the unknown unicast traffic to a single interface.
Thanks for your time and patience 🙂
If you have a question, please do not hesitate to ask me by leaving a comment.
Best Regards.
References :
- http://www.juniper.net/documentation/en_US/junos13.3/topics/concept/rate-limiting-unknown-unicast-forwarding-understanding.html
- http://www.cisco.com/c/en/us/td/docs/switches/lan/catalyst6500/ios/12-2SX/configuration/guide/book/blocking.pdf
- http://packetlife.net/blog/2010/jun/4/blocking-unknown-unicast-flooding/