Last week, while I am analyzing one of the sample that I found it very suspicious, I found SMTP,FTP and C&C passwords of the malware writer and some interesting details. And I decided to share the details with you.
The sample was shared with me by one of our customer. And, the customer said that it looks suspicious but when we analyze with their sandbox, the sample doesn’t do anything.
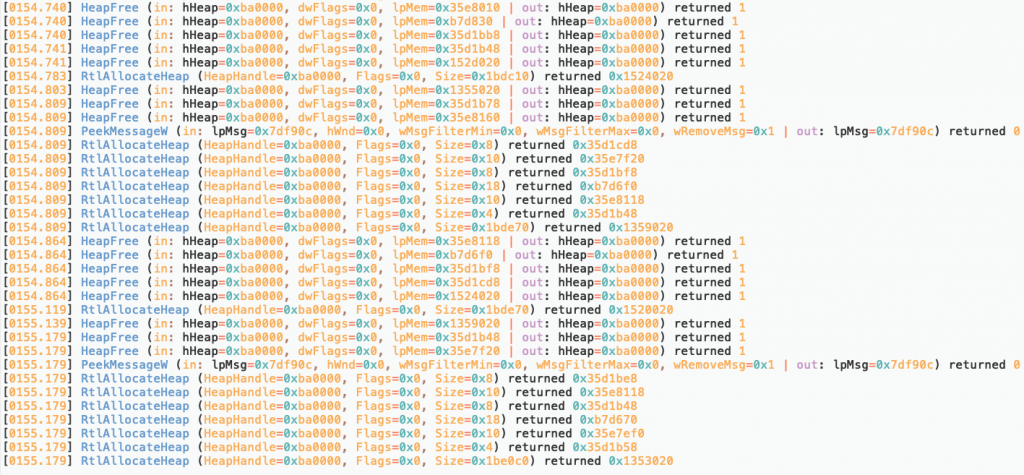
Then, I decided to analyze the sample deeply. Thanks to VMRay Analyzer’s function log feature (I think it is the best product’s feature in sandboxing category ), I realize that it runs into a loop for 300 seconds which contains only RtlAllocateHeap and HeapFree functions.
Usually, evasive malwares use sleep function to bypass sandbox after determining the running environment as sandbox. But, this sample directly jump into a loop for 300 seconds without any control. This behaviour attract me to go further.
I disabled the stop on idle configuration and set the analyze timeout to 10 minutes in order to see what it is going to do after the loop below.
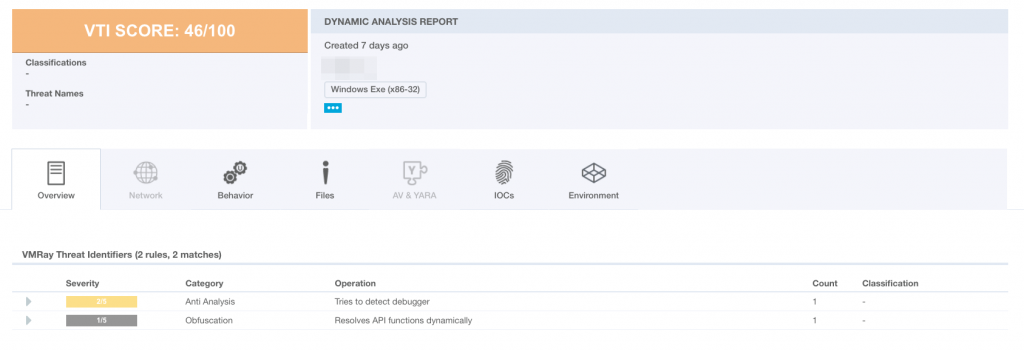
With this configuration VMRay marked the sample as malicious with the %100 confidence as follows.
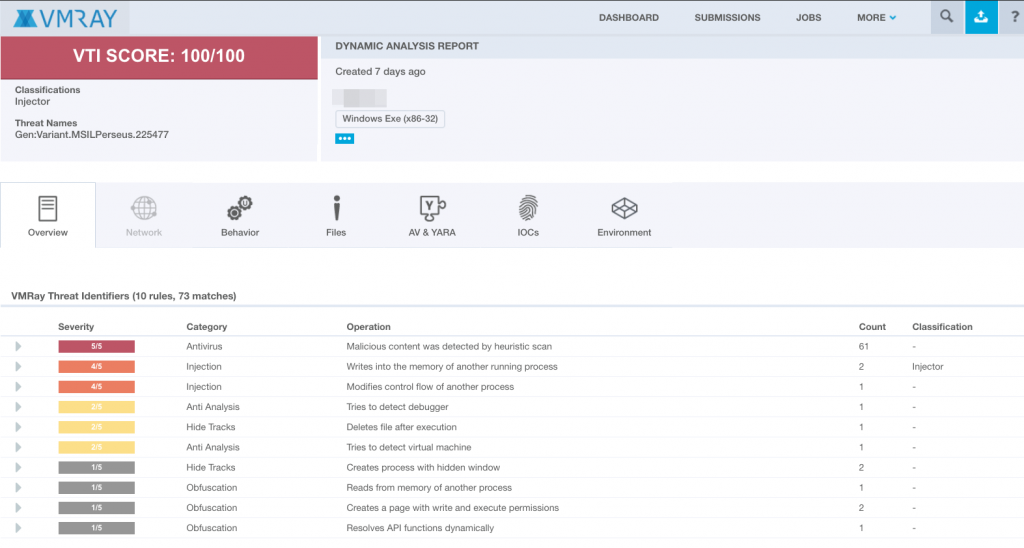
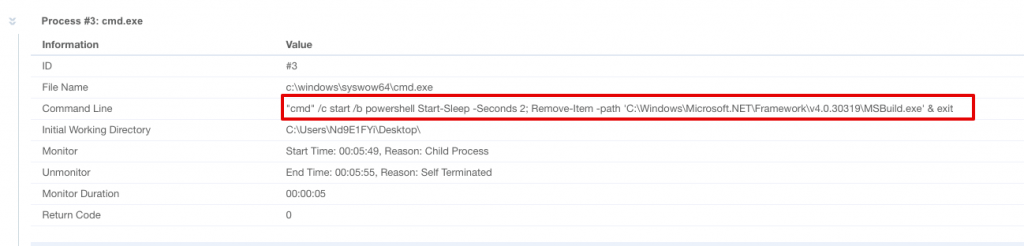
Sample did some process hollowing tricks as below. It executes msbuild.exe with custom shellcode.
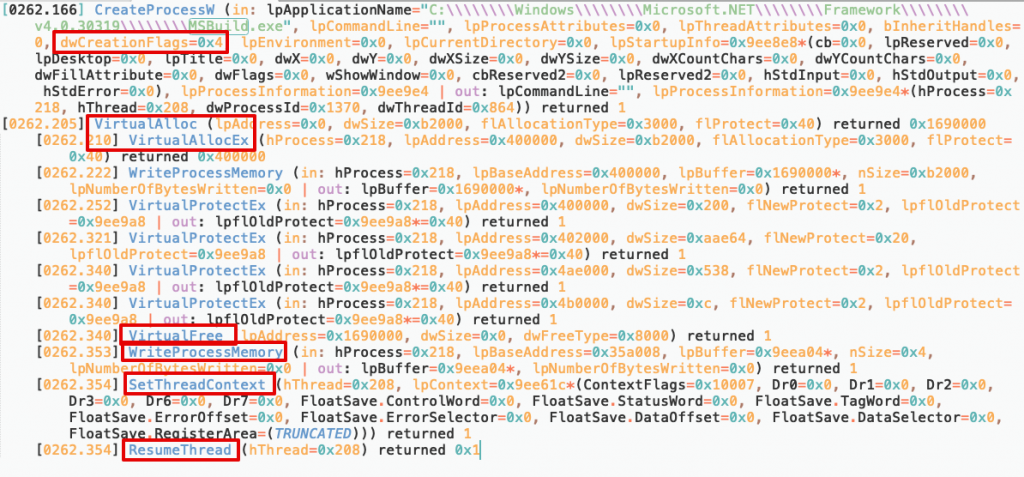
After doing this injection, malware started cmd.exe with the following command to delete msbuild.exe.
There should be a something more. Why a malware writer did this injection then exits without doing anything?
Let’s keep digging.
I turned back to the functions logs of the malware that I exported from VMRay. Then, I investigate what it checks before starting cmd.exe.
Then I realize that malware checks the screen resolution with GetSytemMetrics API then start cmd.exe.
Malware writer must have thought that there shouldn’t be any corporate user without full HD monitor 🙂
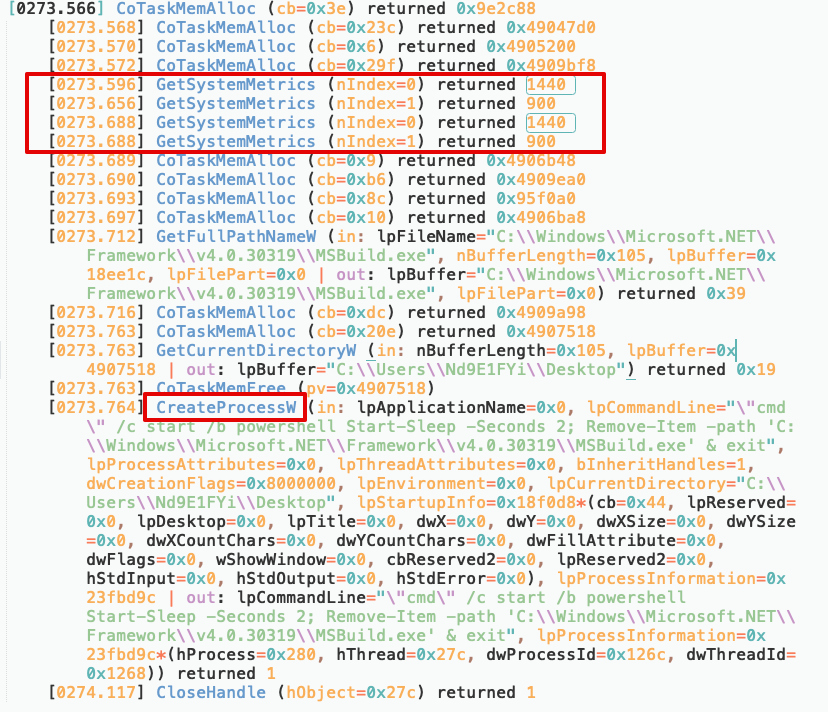
In order to get rid of this screen resolution control, I use VMRay’s prescript feature. By using the script below, I changed the screen resolution higher than FullHD before analysis.
powershell.exe -c "IEX (New-Object Net.WebClient).DownloadString('http://<IP>:8000/ali.ps1'); Set-ScreenResolution -Width 2560 -Height 1600;"
Then, Bingo. Malware started to collect sensitive data from the client, after that it sent the data by e-mail.
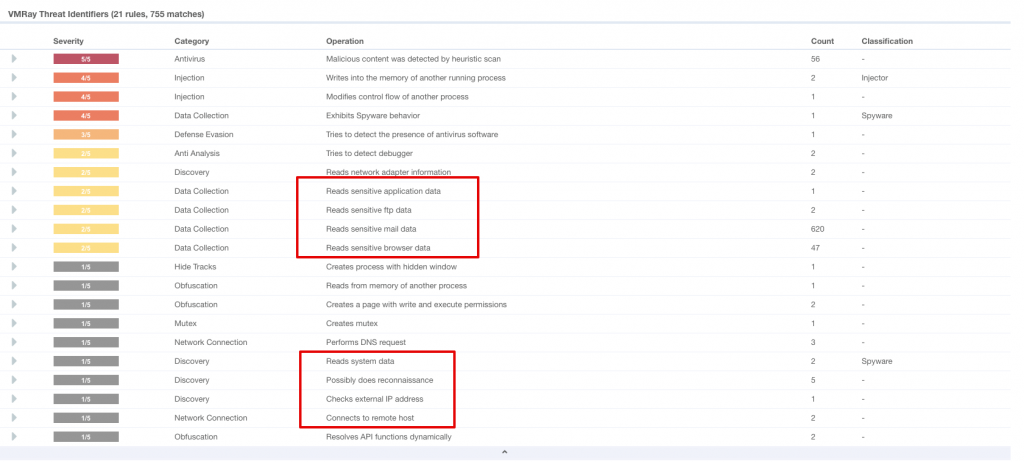
When I checked the connection tab for the network activity I saw the mail server’s domain and IP.
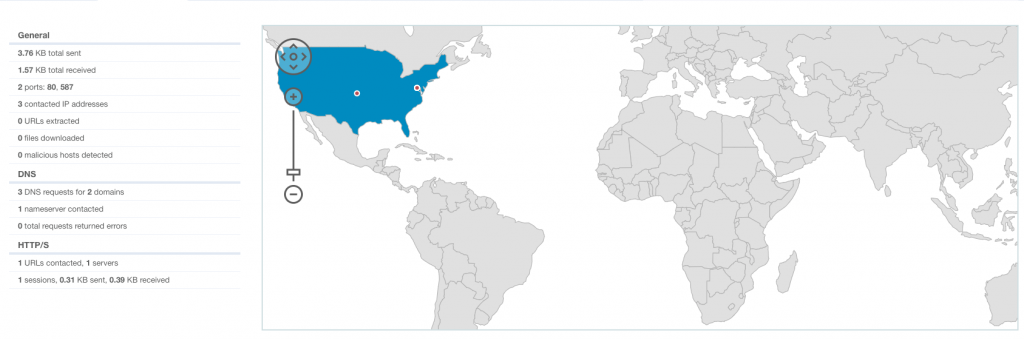
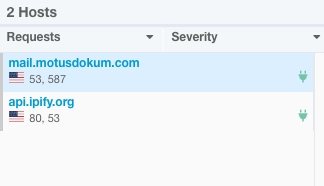
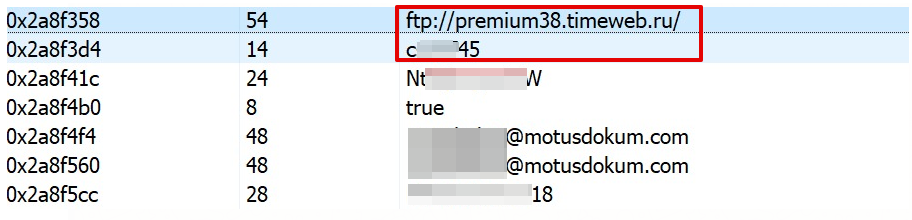
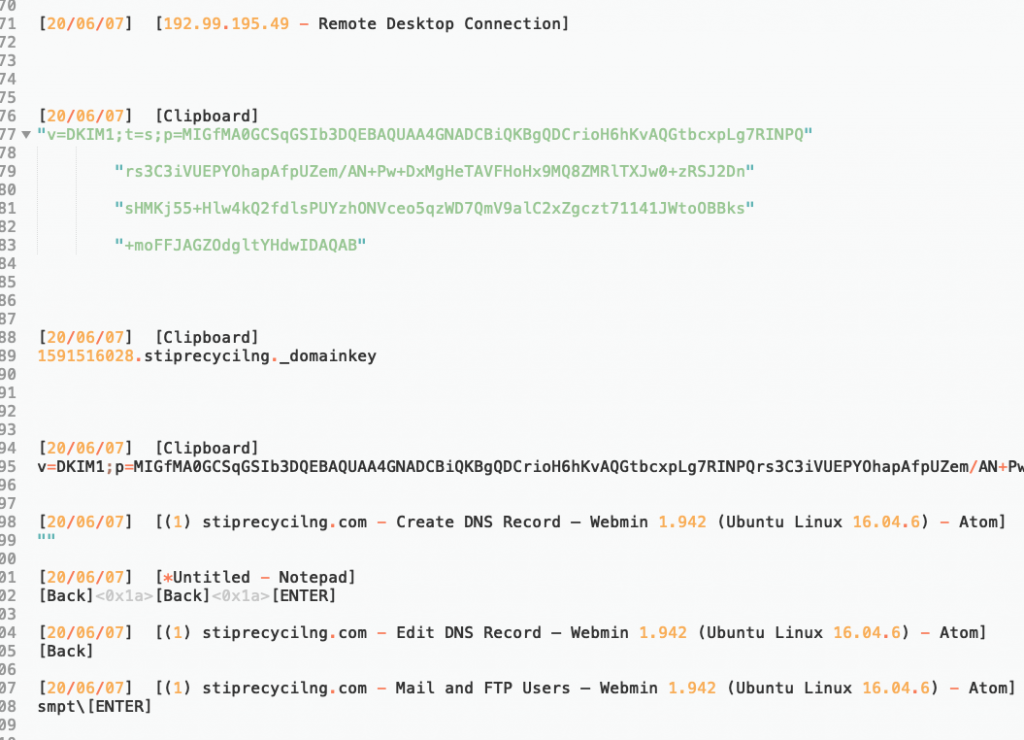
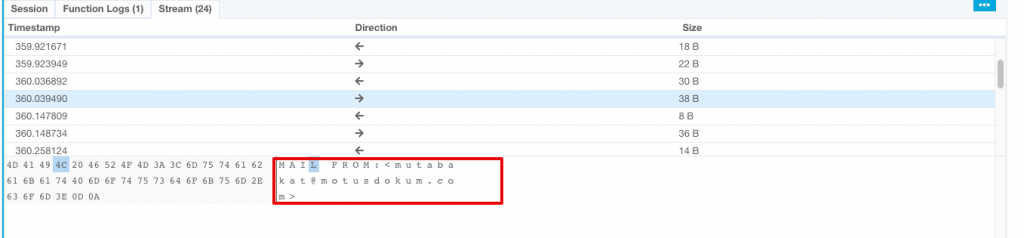
With aid of VMRay network stream feature I saw some interesting data as follows.
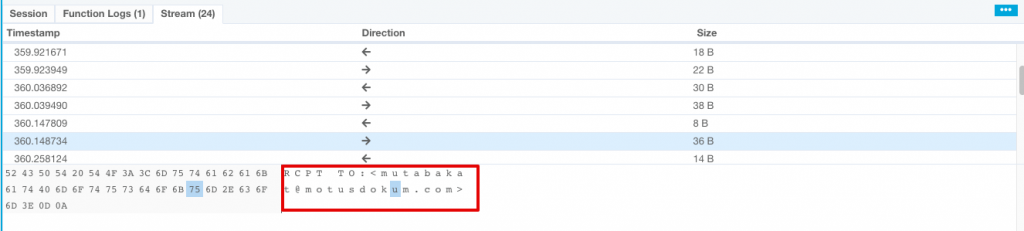
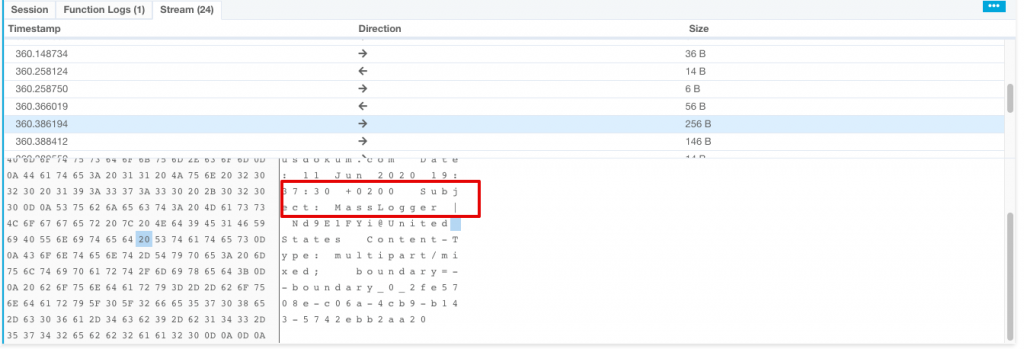
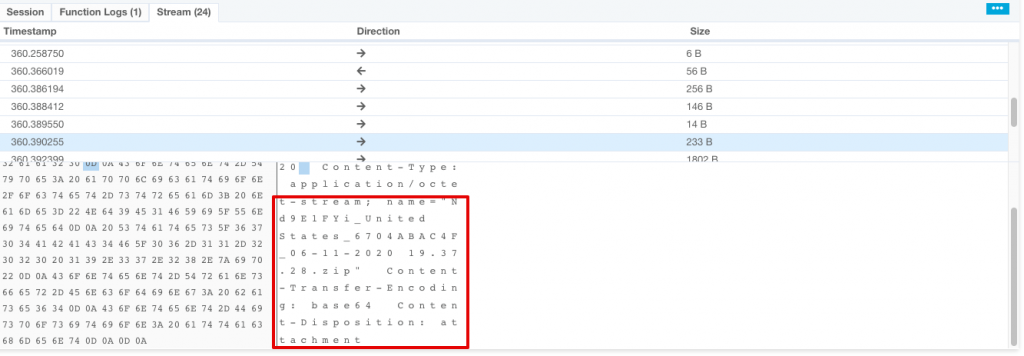
As seen above, attacker uses a Turkish hacked domain to sent the data himself with a zip attachment.
In order to sent an e-mail over a mail server, client have to authenticate with a username and password. To find and verify mailbox’s password I decoded below data then found the password.
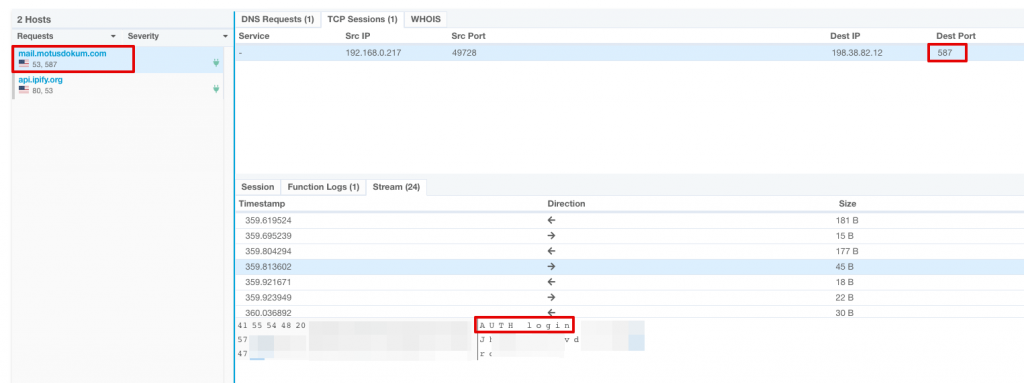
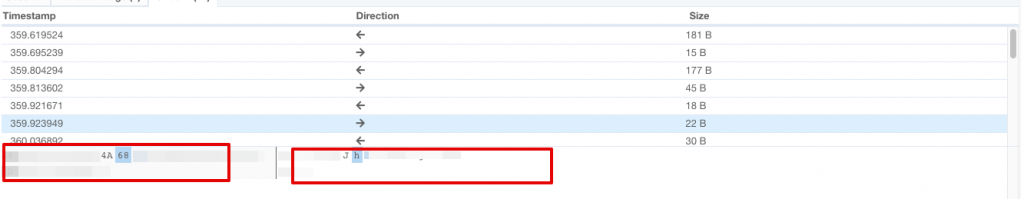
Let’s analyze it dynamically on my malware analysis environment.
Some interesting domain names.
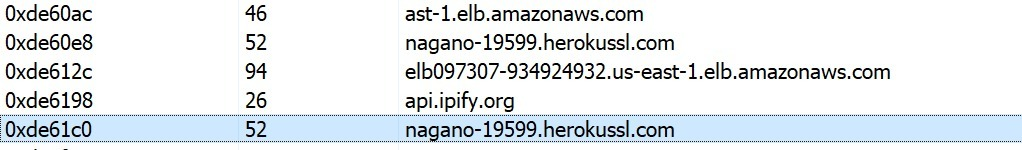
Some interesting strings.
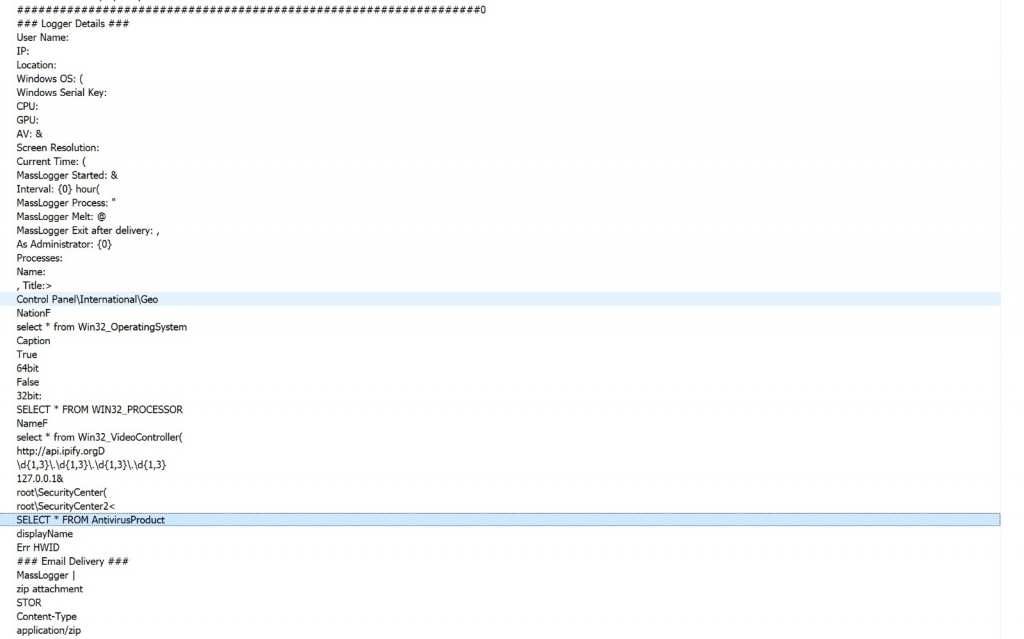
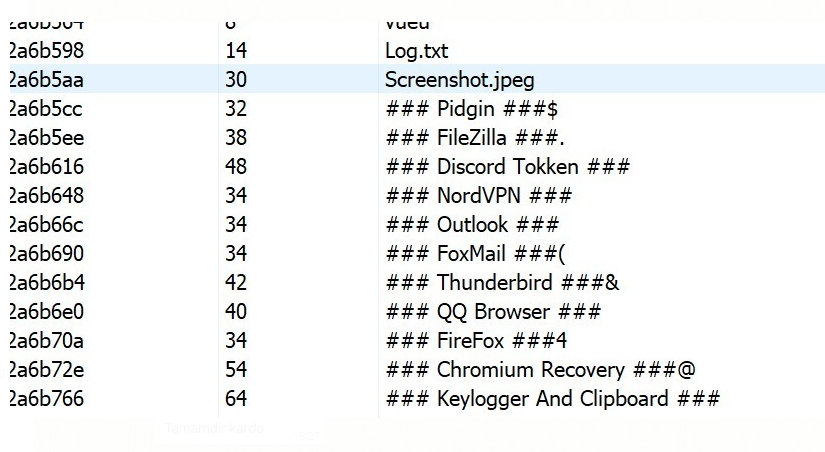
I found a FTP password in memory strings as follows.
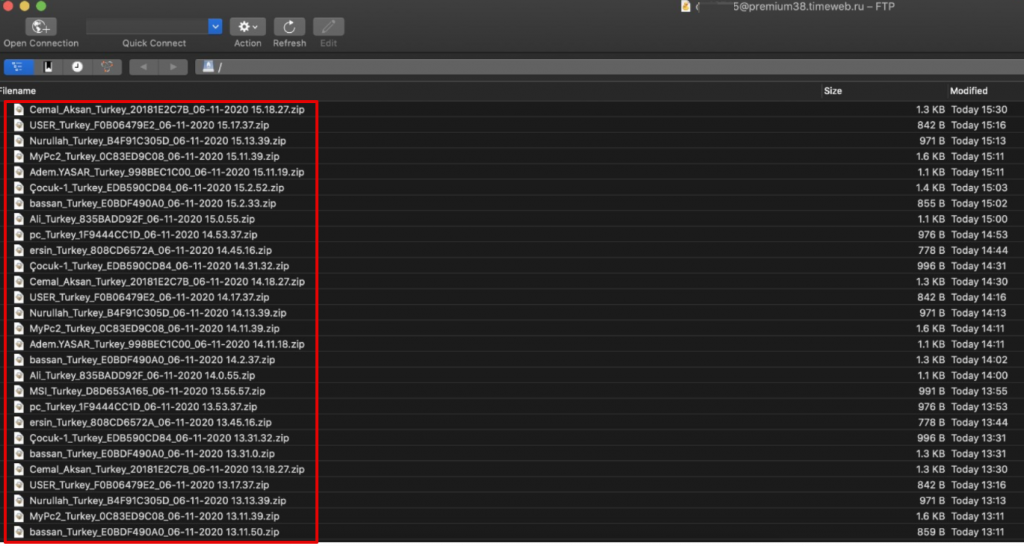
I tried to login and succeeded. There were 310 compromised host from Turkey those are sending browsers credentials and keylogs to the FTP.
Then, I saw a compromised host named as Macintosh, it looks strange because the malware that I analyzed written for Windows OS. That’s why, I download and check the details in Macintosh_United States.zip. ,
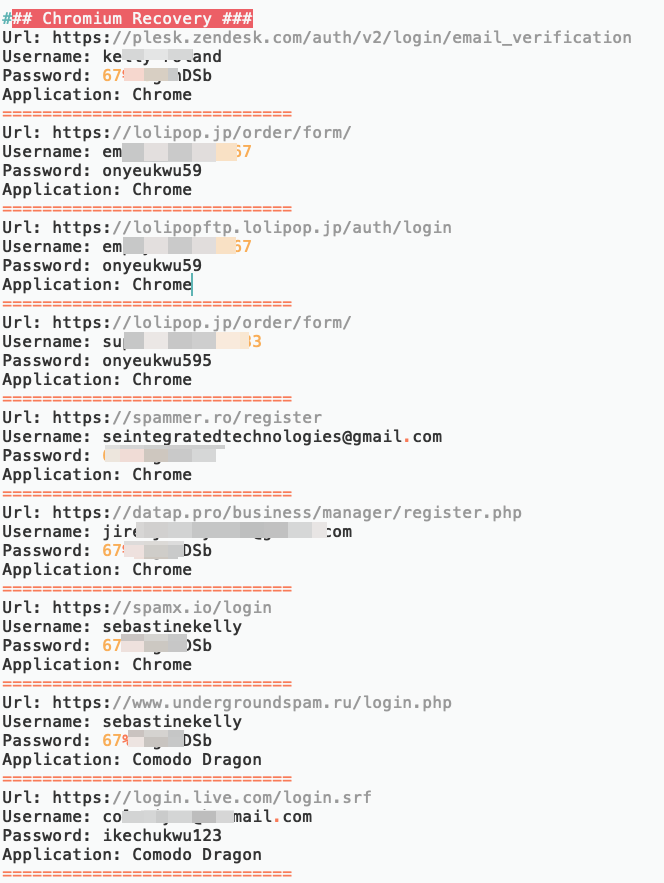
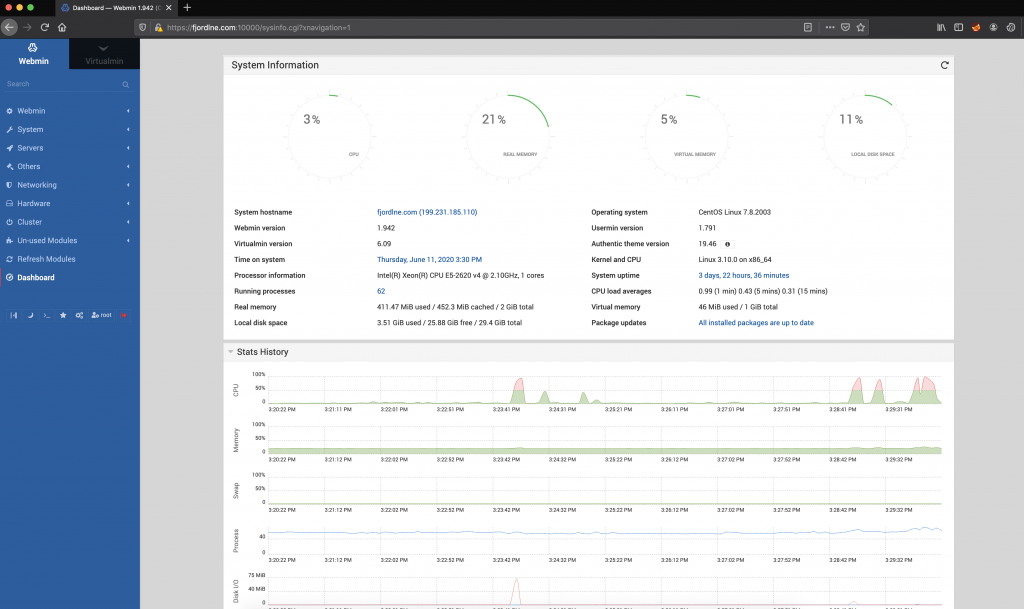
After a short lookup, I unterstand that malware writer execute the malware in his computer then forget to stop it. That’s why, malware collects his whole browser’s saved passwords, Filezilla’s saved credentials and too much intersting keylogs screenshots. 🙂
FTP Creds.
Chrome’s saved credentials.
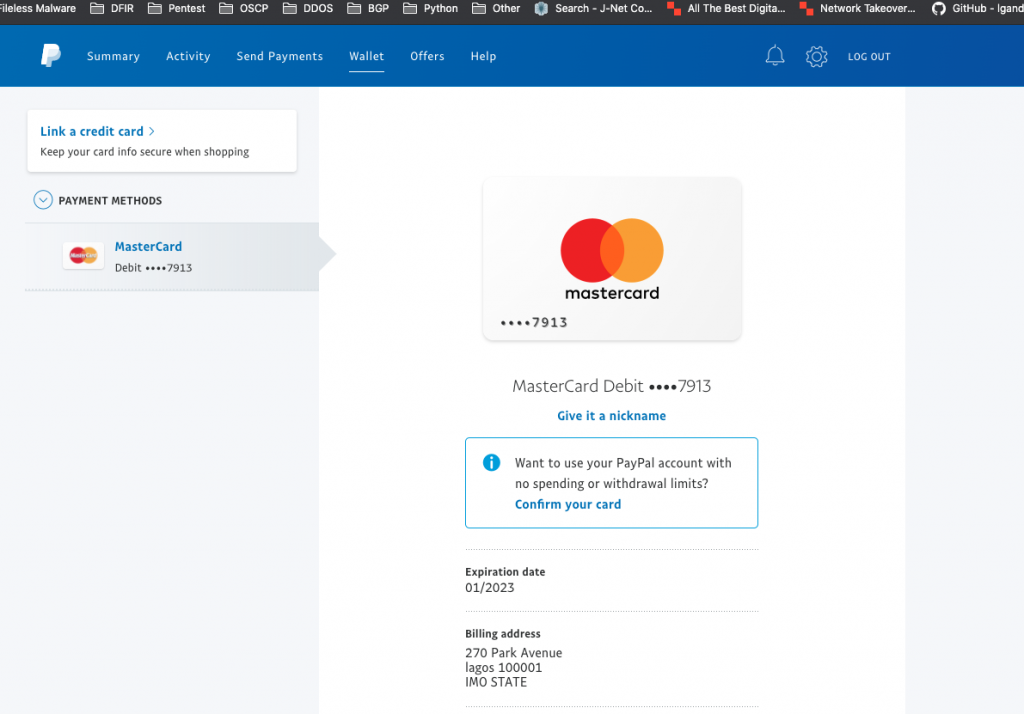
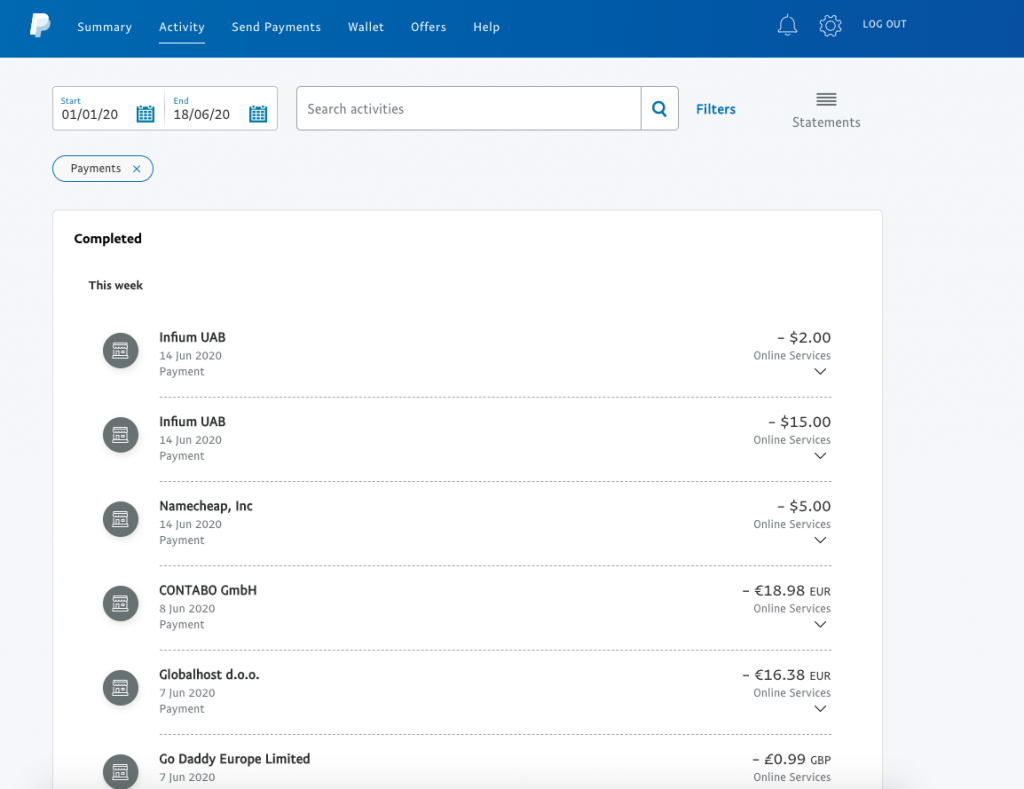
Attackers paypal accounts.
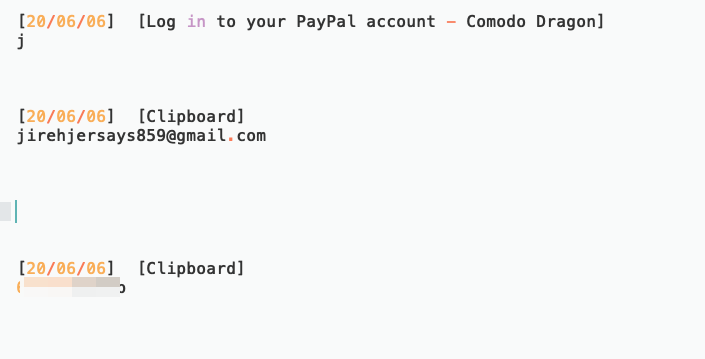
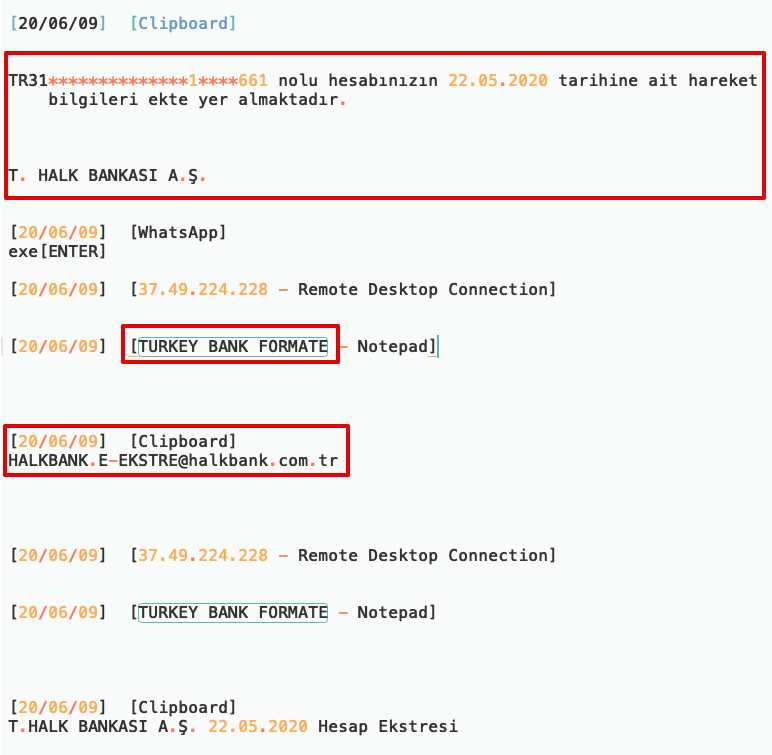
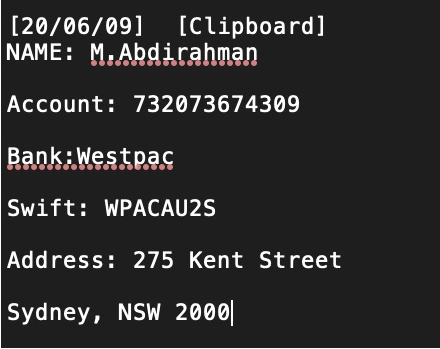
Interesting clipboard data. He is obviously directly targeting Turkish users.
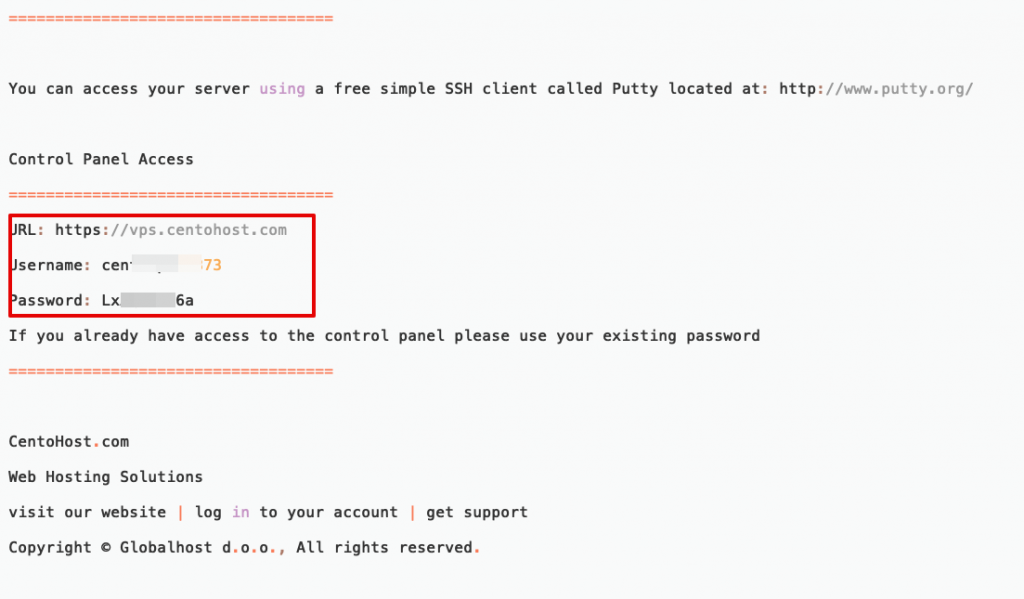
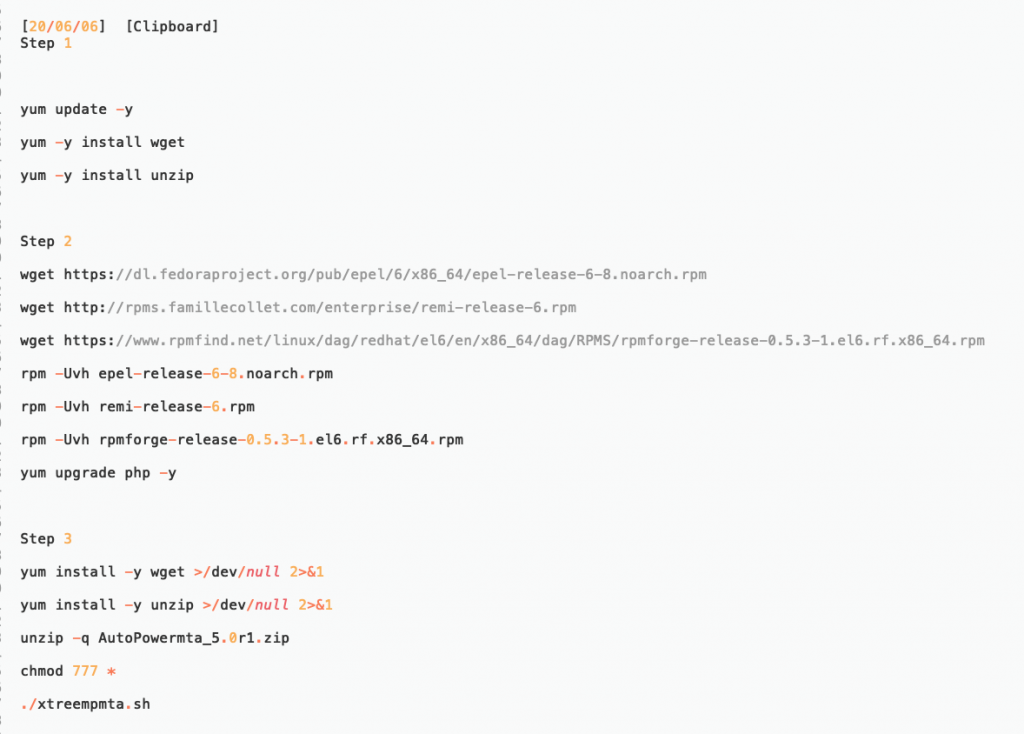
Attackers virtual machines and DNS records.
It looks he is new to Linux 🙂
He is selling keylogger.
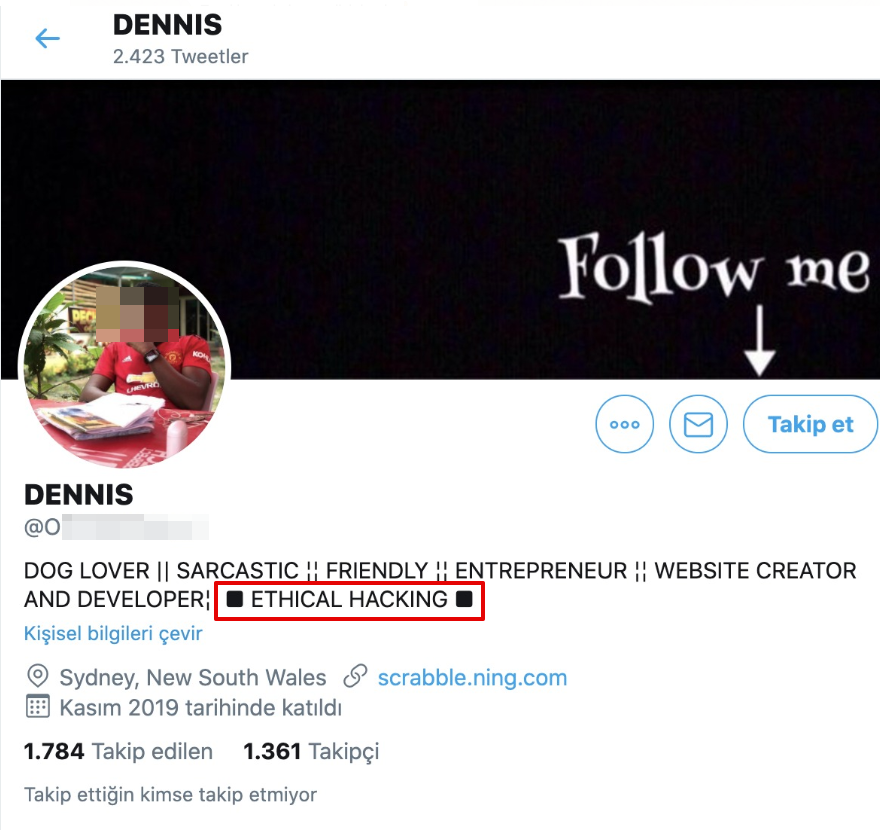
Then finally I found his personal details.
I shared this whole information to show how attackers plan their attacks and how they used the information they gathered.
If you have a question, please do not hesitate to ask me by leaving a comment.
Thanks for reading.