Today, while I am analyzing one of the sample that I found it very suspicious, I found SMTP username and password of the malware writer. And I decided to share the details with you.
The sample was sent by e-mail with a Word attachment as below.
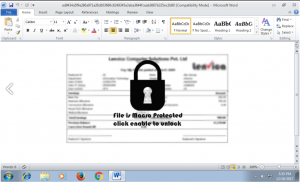
Attachment contains a macro, which is trying to download a PE file from the internet.
Dropped Sample: https://www.hybrid-analysis.com/sample/54c807420c4c64212d8e12653f7cade4a1b140aba23a246db694836349372dcd?environmentId=100
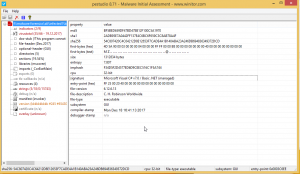
Firstly, I had a look at dropped sample from PEStudio as follows. And I realized that, It was written in C# and complied an hour before It was sent.
I tried to decompile it with .NET Reflector Decompilation tool but it wasn’t successful.
And then, I analyzed the sample with Exeinfo PE application and It can be easily seen that it was obfuscated or packed.
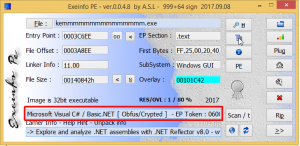
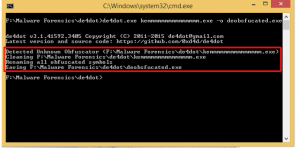
In order to deobfuscate the sample, I used de4dot .NET deobfuscator and unpacker with respect to Gökmen Güreşçi‘s suggestion.
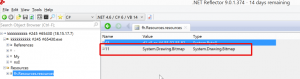
Then I realized in the resources part ,that there was a Bitmap file and the other parts didn’t contain so many codes in it.
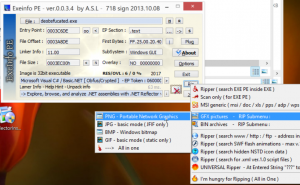
But, I couldn’t find anything worthy in this PNG file. (If someone has an idea about how to analyze PNG file, he can ping me)
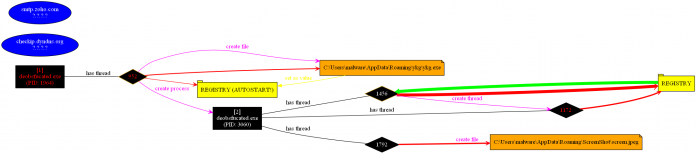
That’s why, I decided to analysis the malware dynamically. Briefly, It modifies the registry to add itself to autostart, tries to identify public IP of the host and tries to connect an SMTP server (mail.zoho.com) with TCP port 587 as seen below.
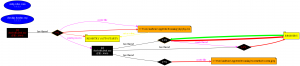
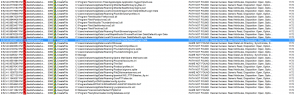
To sum up, it takes screenshots in every minutes, looking for some credentials in the config files and tries to send these information by using SMTP with the user [email protected].
Before giving up, while I was walking around the strings in the memory, I saw interesting strings in the memory as follows.
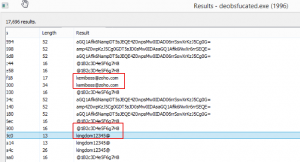
After all, I tried to login https://mail.zoho.com with the password ‘@1B2c3D4e5F6g7H8’ and ‘kingdom12345@’.
Then bingo 🙂
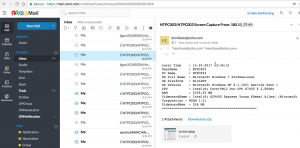
There are too many victims seen in the inbox and some victims were from Turkey. And there is not only screenshots, but also it is logging keystrokes and send them to the attacker. For example, authentication information of the firewall of a victim gathered as below.
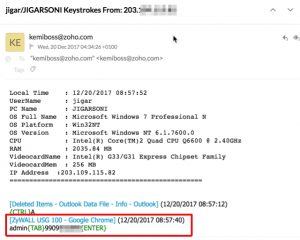
There is an intresting screenshot show us that there is a well known endpoint security installed on one of the victim as below.
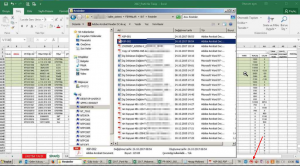
But it is not over. The guy behind this attack, stores his malwares in dropbox as below. And he recreates them with different templates regularly.
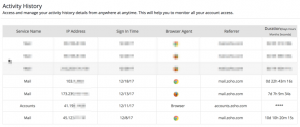
I checked the login activity of the mail box. And, It was obvious that the attacker connects the mailbox from four different countries (Nigeria,United States, Austria, and interestingly Turkey).
Thats all for now 🙂
PS: I shared the sample and details with USOM (TR CERT)