Detecting Macro Enabled Office File
Nowadays, the attackers pushes massive spam campaigns in order to spread their malwares. They use macro enabled spear-phishing office documents as an e-mail attachments. Generally, they are using the files with *.docm and *.xlsm extentions those are designed to spread malwares such as Cryptolocker variants and Odinaff banking trojan. Both of these malwares are very popular and Odinaff is also reported in the wild that SWIFT hack incedents executed by odinaff.
To decrease the risk on our network perimeter from these malwares, It is very important to log and observe its traffic. By default, Intel Security product McAfee NSM doesn’t have a signature for Macro Enabled Office files.
In order to write a custom IPS rules about spear-phishing e-mails that contains a malicious office macro, it is needed to capture and analyze the real traffic.
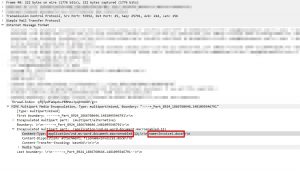
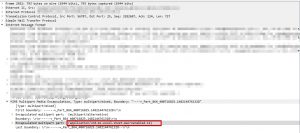
As seen above, the attachment is described in smtp body and its application type is also stored there. It looks enough to check application type in order to detect the malware.
The steps that is required to write custom rules as follows:
Custom attack editor can be found at Policy=>Intrusion Prevention => Advanved => Custom Attacks.
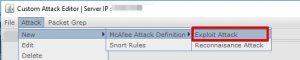
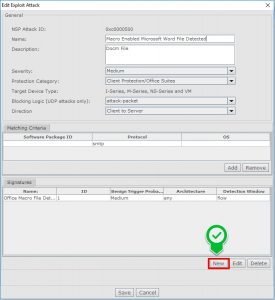
- Firstly, create a condition and then you are able to add acomparison.
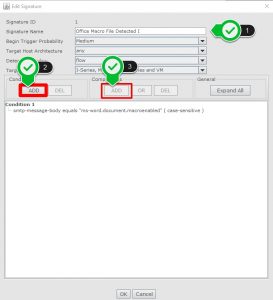
- Select “String Pattern Match” form comparison selection window.
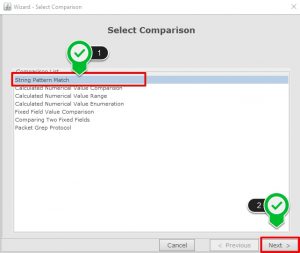
- Select the protocol as SMTP.
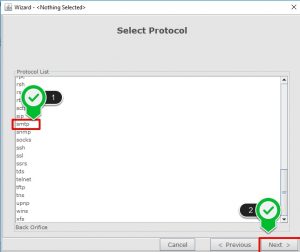
- Select the “Message Body” as protocol field, “Attachment Type” is ANY and “Req Encoding Type” as ANY.
- Then It is needed to specify reqular expression to match.
- For *.docm file use “ms-word.document.macroenabled”
- For *.xlsm file use “ms-excel.document.macroenabled”
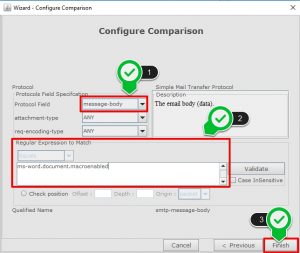
Finally, save and deploy the signature sets.
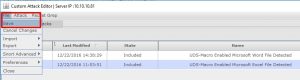
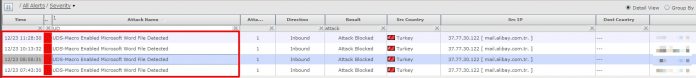
If your criteria hit by an email which contains Microsoft Office Macro, there will be alerts covering this misuse as below.

In default, custom signatures are going to be disabled. If it is needed, you should enable blocking on the signatures after tests.