Dns Amplification Attacks and How Much Vulnerable We are as A Country
Last week, I talked about one of the misuse type of DNS protocol is DNS tunneling. Today, I am going to talk about another misuse of this protocol, named as DNS amplification.
DNS protocol has become the most used attack vector for DDOS purpose due to following reasons.
The reasons that make DNS protocol most used as a DDOS attack vector.
- UDP based protocols don’t have any handshaking dialogues before establishing a session.
- Being a mandatory infrastructure for making Internet based resources more end-user friendly.
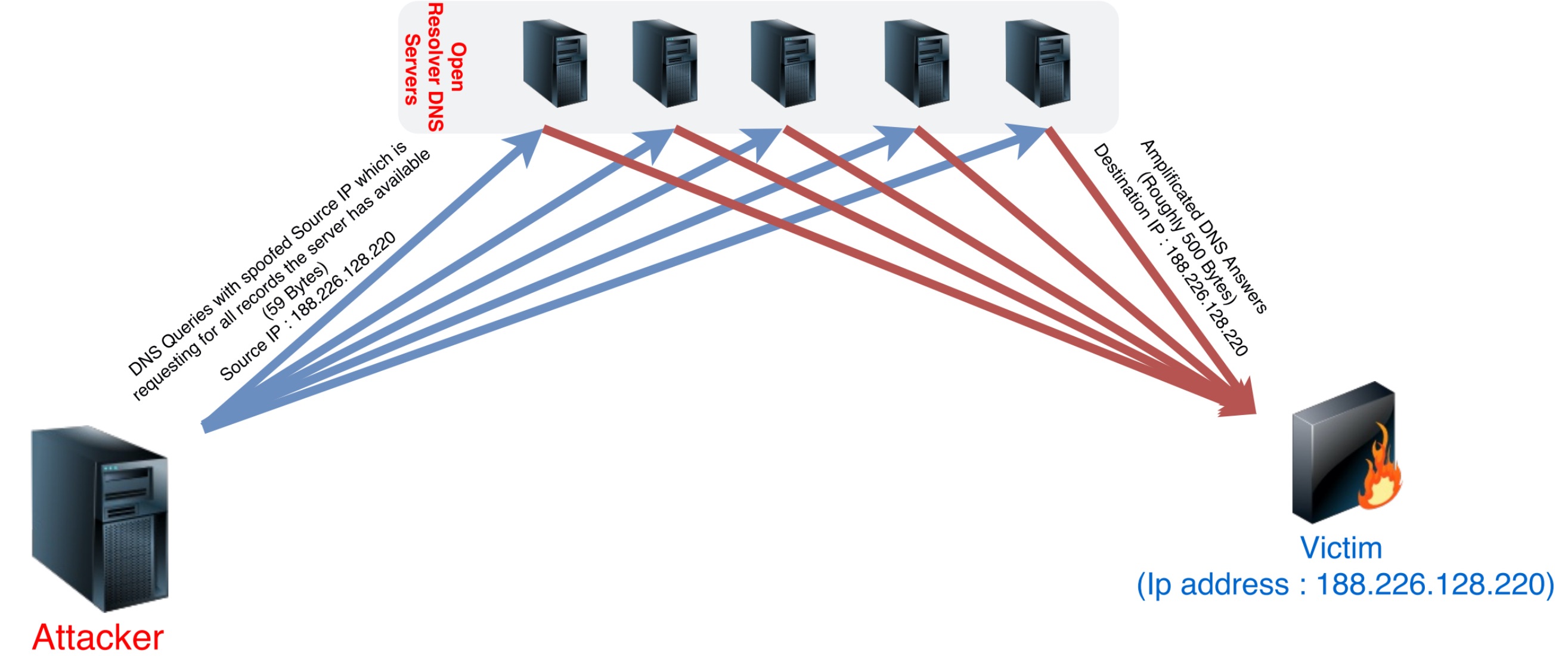
DNS amplification is completely based on spoofing the source IP and generating DNS queries to DNS servers that described the picture below.
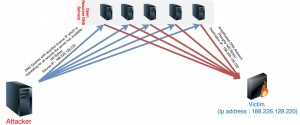
Normal behaviours of a DNS servers are;
- Handle the received packet without any handshaking or authentication.
- Generate an answer to the source of the query.
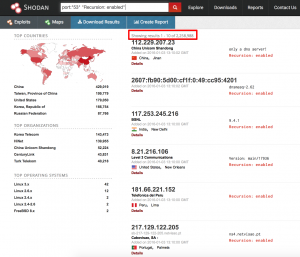
Step 1 : Finding Open Recursive DNS Servers
For data collection about DNS servers, I used Shodan. Shodan is very handy tool for gathering information about mass networks. You can use Shodan for not only mass scan but also to get information about exploits. The number of results about recursive DNS servers are stunning, is following.
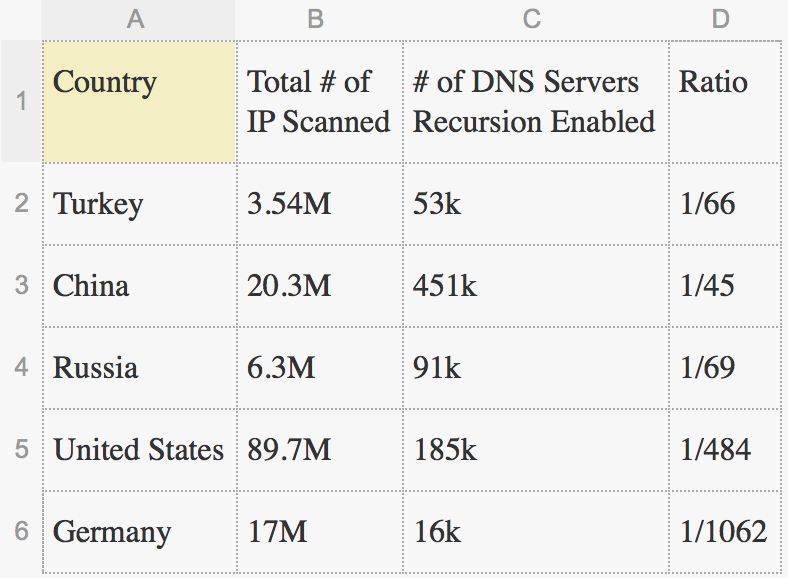
I collect some data with respect to five countries about the volume of DNS servers. The results calculated in the the table below, show us that one of every sixty six IP alive, can answer recursive DNS queries is very scary in Turkey.
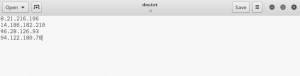
By the way, choose the suitable ones those are best fit to your target and save it to a text file. We will use this text file in order to read the destination from the file. Do not forget that the more DNS server you have, the more your attack volume is getting larger. I choose four DNS servers as an example.
Step 2 : Determining the Suitable DNS Query
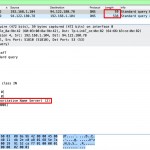
We need to specify that how do we reflect huge answers by asking a simple query to DNS servers. In RFC1035, a DNS record format an types specified as follows.
Picture 4,5 – DNS Record Format and Types
If we generate a query that is asking for NS records of the server, DNS servers are going to generate an answer contains with authoritative name servers they have.
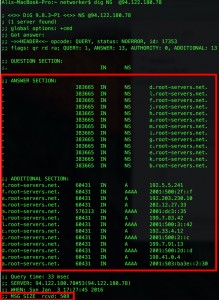
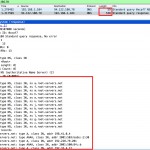
Lets observe what happens on background with aid of Wireshark. As seen below, we got an answer with multiplier of ten. Also note that we are going to use payload pattern of the query in next step.
Picture 7,8 – Wireshark Outputs of a NS Query
Step 3 : Creating DNS Query with Raw Packet Generator
There are a few tools for the aim DNS misuses such as Tsunami and some custom scripts. I use MZ (Mausezahn) which is free raw packet generator “written in C which allows you to send nearly every possible and impossible packet”. The payload pattern that we generate in Step 2 can be used like following.
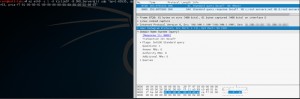
To spoof the source IP, -A parameter has to be used.
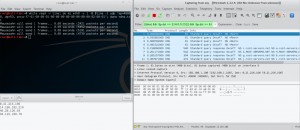
Step 4 : Reading the DNS List from A Text File in MZ
“While loops” can be used for reading destination addresses from a text file. As seen in picture, If source IP isn’t specified, MZ will use your interface IP as a source. So, if we were successful to generate a packet, we are going to observe the answer as well.
Step 5 : Action! Lets Reflect the Answers to Victim
I choose one of my vps as a victim and I choose vps’ IP as a source. Then send the NS queries to the DNS servers written in the text file.
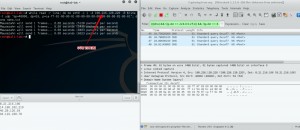
Finally, The answers of the spoofed queries reflected to the victim as following.
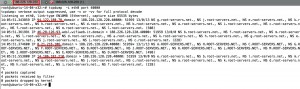
As a result, I got about 6 Mbps reflected traffic with my home Adsl connection (NAT disabled) that has only “1 Mbps” upload speed. The purpose of this post is to show how easy and dangerous DNS amplification attacks are.
If you have a question, please do not hesitate to ask me by leaving a comment.
Edit : Please also note that do not forget to secure your DNS server by writing ACL for recursion and close your server to “. (dot) and NS” type queries .
Best regards.


there ‘s a point that we should remember, every single recursive query will make a iterative query for root or neigboor servers. I think which badass problem is couldn’t forward all queries without to fill all bandwith of network or before not coming to DNS servers. Need more packet processing or new technologies for understanding fakes*…
* Turkish mantality; Why would I want to resolve the other sites from outer n my country? Sites owner should make a sites for my country. Sources’re always being from outside…