The SMB Protocol (Server Message ) is the protocol which is used for sharing file and print resources between machines and also that allows applications on a computer to read and write to files and to request services from server programs in a computer network. It is served from the TCP port number 445.
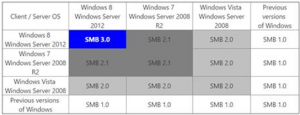
It is widely used in approximately all corporate networks and mid-sized companies. SMBv1 published about three decades ago, and it is still enabled in Windows10 by default. As shown in the table below, It can easily seen that SMBv1 is not required after Windows Server 2008.
There is a rumour that the hacking group known as the Shadow Brokers will publish a lot of windows zero days in the near future. Even existence of a Windows SMB exploit has not been confirmed, US-CERT published a security bulletin as “SMB Security Best Practices” in January 16, 2017.
US-CERT Security Bullettin: https://www.us-cert.gov/ncas/current-activity/2017/01/16/SMB-Security-Best-Practices
On the other hand, Microsoft has published a SMB security enhancement advices as follows.
https://technet.microsoft.com/en-us/library/dn551363(v=ws.11).aspx
Okay, let see how easy to misuse SMB traffic with an old exploit in an enterprise networks.
Step 1 – Being Familiar with Related Metasploit Module
There is a module which is located in “exploit/windows/smb/smb_relay” and reported as the exploit of MS08-068 Microsoft Windows SMB Relay Code Execution.
This module is discribed as a relay for SMB authentication requests to another host, gaining access to an authenticated SMB session if successful. If the connecting user is an administrator and network logins are allowed to the target machine, this module will execute an arbitrary payload. To exploit this, the target system must try to authenticate to this module.
Implementation and usage explained in the URL below.
https://www.rapid7.com/db/modules/exploit/windows/smb/smb_relay
Step 2 – Exploit
The easiest way to force a SMB authentication attempt is by embedding a UNC path (\\SERVER\SHARE) into a email message. When the victim views the email, their system will automatically connect to the server specified in the share (the IP address of the system running this module) and attempt to authenticate.
We specify the lab paramaters as below.
Attacker : 10.10.10.2 Admin : 10.10.10.10 (We will use its NTLM responses to relay) Victim : 10.10.10.6
After specifying parameters and executing exploit command, the module will start to listen for SMB authentication requests. When it receives a SMB authentication request, it will use this request to authenticate to the victim machine and send back a login failure response to the Admin. If the authentication is successful, It will transfer the executable that you created before to reverse shell.
Step 3 – Observations
As seen the picture below, after getting the session, the attacker is able to do anything that relayed admin user can do.
- He can list your process tree and migrate himself to any system process.
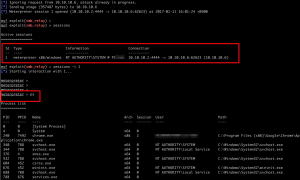
- He can read or write to any path or download any file, meanly, he can take a tour in victim’s file system.
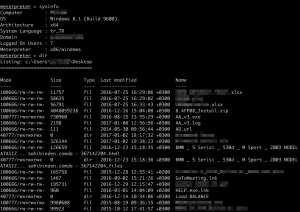
The last but not least one(ohh stop, it is not toefl writing part 🙂 ) Finally, if the victim has a microphone, he can listen and record the sounds from mic 😛
I needed to put here a reminder that; It is my first blog post other than Network and Security ones. Thats why, your feedback will be very worthy to make clear my fault.
If you have a question, please do not hesitate to ask me by leaving a comment.
https://www.us-cert.gov/ncas/current-activity/2017/01/16/SMB-Security-Best-Practices
https://technet.microsoft.com/en-us/library/dn551363(v=ws.11).aspx

It’s very good article.Useful and clear.
Thanks for your effort.